2024 VCON Challenge: Data Minimization
Data minimization is a privacy and data protection principle that aims to limit the collection, processing, and retention of personal data to what is strictly necessary for a specific purpose. The principle of data minimization is based on the idea that organizations should only collect, use, and store the minimum amount of personal data required to achieve a legitimate purpose, and should avoid collecting or retaining excessive or irrelevant data.
Data minimization is a key component of many privacy laws and regulations, including the European Union’s General Data Protection Regulation (GDPR). It is closely related to other data protection principles, such as purpose limitation and storage limitation.
The Challenges:
- Best Redaction: Take the series of vCons we give you, and remove all the personal identifiable information. Extra points for delivering it in the form of a conserver link.
- Best Detection: Take the series of vCons we give you, and list all the personal identifiable information. Extra points for delivering it in the form of a conserver link.
What is a vCon?
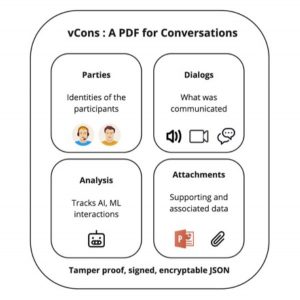
A vCon (Virtual Conversation Container) is a standard container for storing and managing conversational data (such as transcripts and multimedia files) generated in business communication, particularly in customer-facing organizations. It contains metadata, dialog, analysis and attachments portions, which include information such as participant identification, conversation contents, sentiment analysis, context documents, and integrity checking information. vCons can be used to ease service integration, help with data management and privacy, and serve as input for communication analysis and machine learning tools. They are designed to be digital assets that are versioned and signed for data integrity and provenance. The use of vCons helps lower the cost and speed deployment of analysis tools and eases customer analysis across different product lines.
vCons safely and securely carry conversations from the network elements that create them to the applications that analyze them, enabling responsible management of the most personal of data.
Resources
Our Hack Introduction Video